| .github | ||
| docs | ||
| install | ||
| src | ||
| static-data | ||
| tests | ||
| .dockerignore | ||
| .env | ||
| .gitignore | ||
| .gitlab-ci.yml | ||
| .onionr.yml | ||
| AUTHORS.MD | ||
| CODE_OF_CONDUCT.md | ||
| CONTRIBUTING.md | ||
| Dockerfile | ||
| ISSUE_TEMPLATE.md | ||
| LICENSE.txt | ||
| make-release.sh | ||
| Makefile | ||
| onionr.sh | ||
| README.md | ||
| requirements-notifications.in | ||
| requirements-notifications.txt | ||
| requirements.in | ||
| requirements.txt | ||
| run-windows-dev.bat | ||
| run-windows.bat | ||
| run_tests.sh | ||
| SECURITY.md | ||
| setprofile.sh | ||
| start-daemon.sh | ||

Privacy Respecting Communication Network 📡



| Install | Features | Screenshots |
| Docs/web copy | Get involved | Onionr.net/.onion |
The main repository for this software is at https://GitLab.com/beardog/Onionr/
The GitHub repository is a mirror, do not submit PRs or issues there.
About
Onionr ("Onion Relay") is a decentralized/distributed peer-to-peer communication network, designed to be anonymous and resistant to (meta)data analysis, spam, and corruption.
Onionr stores data in independent packages referred to as 'blocks'. The blocks are distributed to all interested nodes. Blocks and user IDs cannot be easily proven to have been created by a particular user. Even if there is enough evidence to believe that a specific user created a block, nodes still operate behind Tor or I2P and as such cannot be trivially unmasked. The anonymity is achieved by a stateless network with no given indication of what node a block came from or even the user ID.
Through long-term traffic analysis, a well funded adversary may discover the most probable node(s) to be creating a set of related blocks, however doing so would only lead them to a node behind Tor or I2P. As the first node that a block appears on is almost always not the creator of the block, there is plausible deniability regarding the true creator of the block.
Users are identified by ed25519/curve25519 public keys, which can be used to sign blocks or send encrypted data.
Onionr can be used for mail, as a social network, instant messenger, file sharing software, or for encrypted group discussion.
The whitepaper (subject to change prior to alpha release) is available here.
Main Features
- 🌐 Fully p2p/decentralized, no trackers or other single points of failure
- 🔒 End to end encryption of user data
- 📢 Optional non-encrypted blocks, useful for blog posts or public file sharing
- 💻 Easy HTTP API for integration to websites
- 🕵️ Metadata analysis resistance and anonymity
- 📡 Transport agnosticism (no internet required)
Onionr ships with various application plugins ready for use out of the box:
Currently usable:
- Public anonymous chat/message board
- Simple webpage hosting - Will be greatly extended
- File sharing (Work in progress)
Not yet usable:
- Instant messaging
Onionr API and functionality is subject to non-backwards compatible change during pre-alpha development
Screenshots
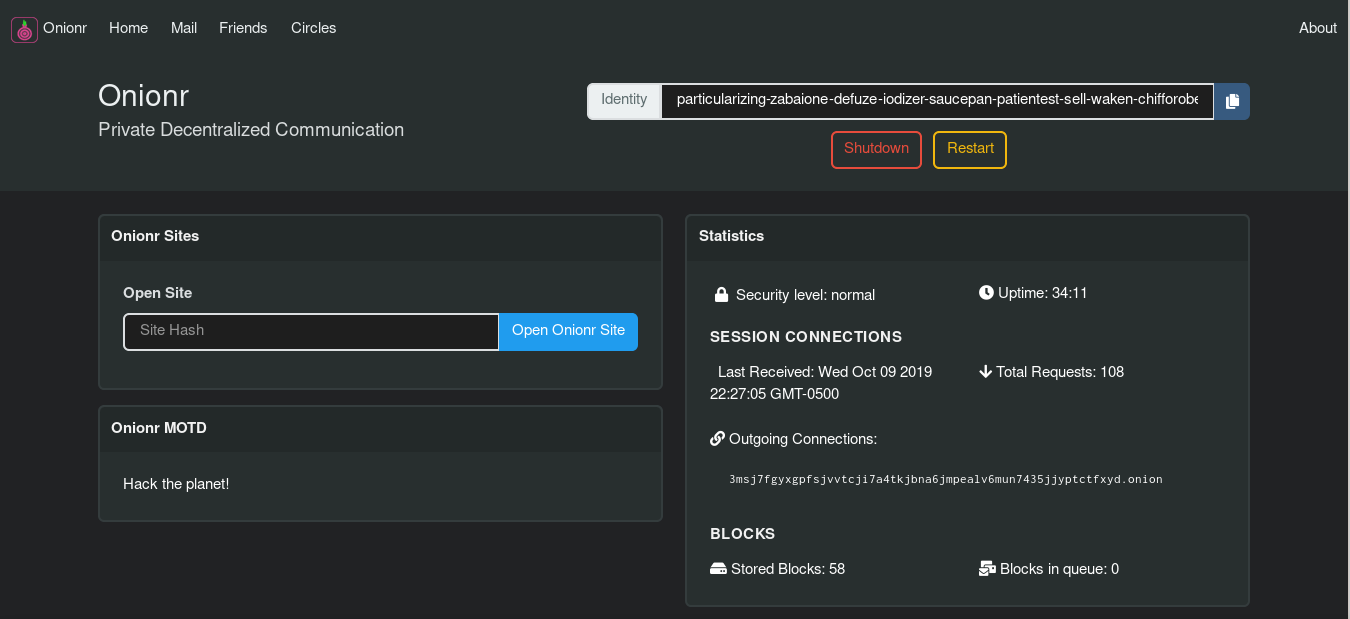
Home screen
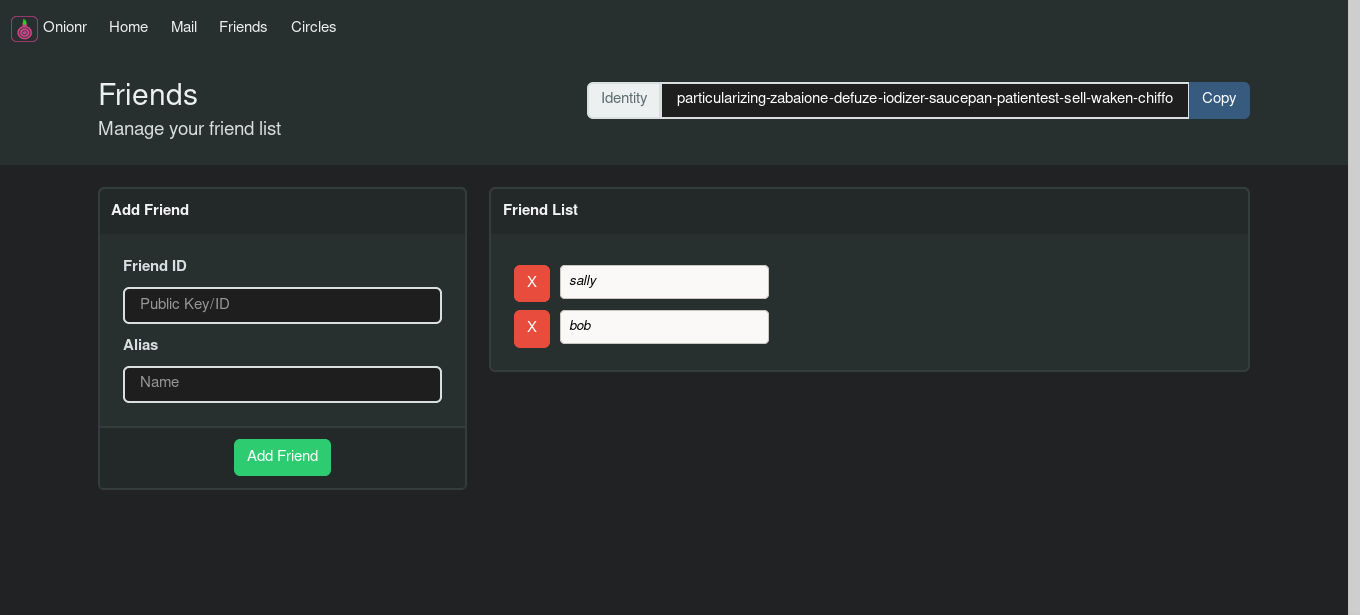
Friend/contact manager
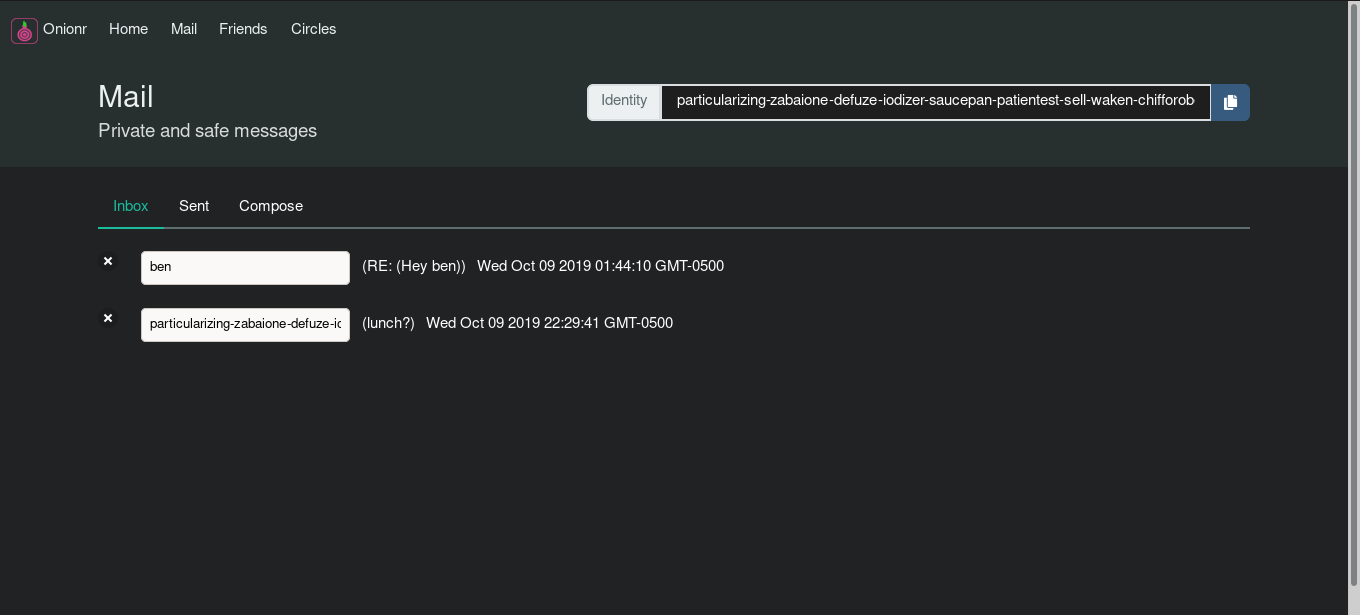
Encrypted, metadata-masking mail application. One of the first distributed mail systems to have basic forward secrecy.
Documentation
More docs coming soon.
Install and Run on Linux
The following applies to Ubuntu Bionic. Other distros may have different package or command names.
$ sudo apt install python3-pip python3-dev tor
- Have python3.7+, python3-pip, Tor (daemon, not browser) installed. python3-dev is recommended.
- Clone the git repo:
$ git clone https://gitlab.com/beardog/onionr - cd into install direction:
$ cd onionr/ - Install the Python dependencies (virtualenv strongly recommended):
$ pip3 install --require-hashes -r requirements.txt - (Optional): Install desktop notification dependencies:
$ pip3 install --require-hashes -r requirements-notifications.txt
(--require-hashes is intended to prevent exploitation via compromise of PyPi/CA certificates)
Run Onionr
- Run Onionr normally:
$ ./onionr.sh start - Run Onionr in background as daemon:
$ ./start-daemon.sh - Open Onionr web interface
$ ./onionr.sh openhome - Gracefully stop Onionr from CLI
$ ./onionr.sh stop
Contact
Email: beardog [ at ] mailbox.org
Onionr Mail: particularizing-zabaione-defuze-iodizer-saucepan-patientest-sell-waken-chifforobe-embonpoint-aquanaut-chambermaid-barky-fumer-jolt-biotic
Help out
Everyone is welcome to contribute. Help is wanted for the following:
- Development (Get in touch first)
- Creation of a shared lib for use from other languages and faster proof-of-work
- Android and IOS development
- Windows and Mac support (already partially supported, testers needed)
- Bug fixes and development of new features
- Testing
- Translations/localizations
- UI/UX design
- Running stable nodes
- Security review/audit
- Automatic I2P setup
Contribute money:
Donating at least $3 gets you cool Onionr stickers. Get in touch if you want them.
Bitcoin: 1onion55FXzm6h8KQw3zFw2igpHcV7LPq (Contact us for a unique address or for other coins)
Monero: 4B5BA24d1P3R5aWEpkGY5TP7buJJcn2aSGBVRQCHhpiahxeB4aWsu15XwmuTjC6VF62NApZeJGTS248RMVECP8aW73Uj2ax
USD (Card/Paypal): Ko-Fi
Note: probably not tax deductible
Security
Onionr is pre-alpha. This means it is unstable, probably insecure, and experimental.
No matter how good Onionr and other software gets, there will always be ways for clever or well-funded adversaries to break your security.
Onionr does not protect your identity if you associate your user ID with your name either on Onionr or elsewhere.
Do not rely on Onionr or any other software to hold up if your life or liberty are at stake.
Licenses and Branding
Onionr is published under the GNU GPL v3 license, except for the logo.
The Tor Project and I2P developers do not own, create, or endorse this project, and are not otherwise involved.
Tor is a trademark for the Tor Project. We do not own it.
Onionr Logo
The Onionr logo was created by Anhar Ismail under the Creative Commons Attribution 4.0 International License.
If you modify and redistribute our code ("forking"), please use a different logo and project name to avoid confusion. Please do not use the project name or logo in a way that makes it seem like we endorse you without our permission.




